Eclipse Biscuit
Eclipse Biscuit is an authorization token with decentralized verification, offline attenuation and strong security policy enforcement based on a logic language
Get startedEclipse Biscuit is an authorization token with decentralized verification, offline attenuation and strong security policy enforcement based on a logic language
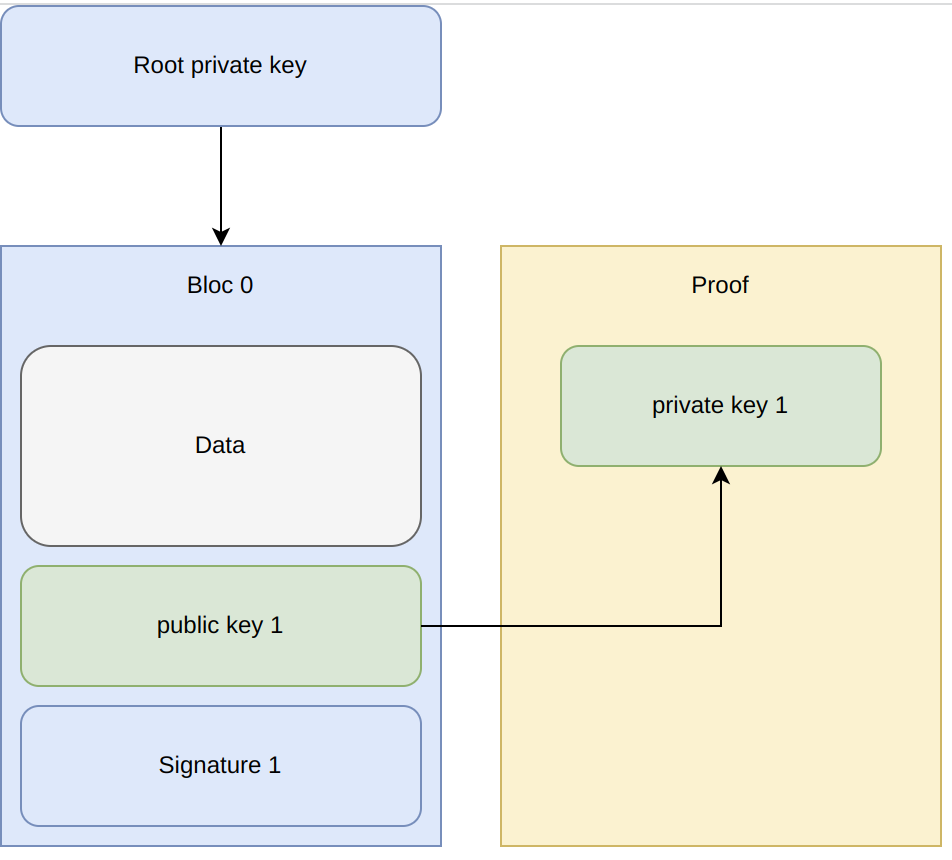
Get startedBiscuit tokens are signed with public key cryptography: any application knowing the public key can verify the token
If you hold a valid token, you can generate a new one with less rights, like restricting write access or adding an expiration date
Authorization policies are written in a logic language. They can be provided by the application, or transported by the token (attenuation)
Eclipse Biscuit is naturally suited for capabilities based authorization, by carrying a token customized for the request. But you can also provide verification side ACLs as Datalog
All tokens come with unique revocation identifiers, that can be used to reject that token and all the tokens attenuated from it
Eclipse Biscuit is available in Rust, Haskell, Go, Java, JS (node & browser), WebAssembly, C, Python, C#… All you need for a new implementation is a Protobuf generator and Ed25519 signing. The specification comes with a list of predefined test cases
Test authorization policies in Datalog:
Eclipse Biscuit is the result of the help of dozens of contributors over the years, patiently refining the specification and implementations. The project is maintained and led by:

Geoffroy has worked on distributed systems security for over a decade, and is now a Senior Staff Engineer at Apollo GraphQL. You will often find him deep in discussions on protocols and cryptography.

Clément is a functional programmer working at Outscale. He loves discussing about FP, distributed systems, cloud architecture, and dogs obviously.